CYBERSECURITY SPECIALIST
1. APPLY
2. PASS ASSESSMENT & INTERVIEW
3. ENROLL & BEGIN PROGRAM

PART-TIME/FULL-TIME PROGRAM

$76,000

504,316

CYBER SECURITY SPECIALIST (Full Time 14 Weeks / Part Time 24 Weeks)
Live Instruction
Up to 10 hours of live technical instruction every week for cohort-based program students as well as weekly coaching sessions for self paced programs. In addition to technical instruction and lab building, students also work with our career services team for professional career coaching, technical and behavioral practice interviews, and professional career maps and guidance check-ins.
Tools You’ll Use
Command line tools, Wireshark, metasploit, nmap, port scanner, packet sniffer, network scanner, VPNs, Firewalls, Password cracking, Wifi Cracking, text editors, Rubber Ducky, spam blockers, CLI, shodan, OpenVAS, CVSS, CVE, Keyloggers, AV Tools, IPSec, Hashing, GHDB, Domain Lookup, Nessus Scanner.
Intro to Networking for Cyber Security
Networking is the foundation of many IT specialties and provides a pathway to different careers such as Cyber Security. Cyber Security is one of the biggest growth areas with the need for qualified specialists increasing every day. This course covers the basic networking principles required to transition into the Cyber Security course. Let’s get started on your journey into the realms of computer networking and cyber security! #LevelUp
GETTING STARTED AND PREPARING FOR SUCCESS
You will begin with gaining insights into becoming a Cyber Security Professional, understanding your career path options, and getting started with the program!
CORE NETWORKING CONCEPTS
In the Core Networking Concepts module we cover frames, MAC addresses and broadcast domains. Then we will move into IPv4/IPv6, ARP, routing and wireless LANs.
SYSTEMS AND SECURITY
The Systems and Security module covers virtualization, cloud technologies and operating systems. Several networking security concepts will be introduced including Access Control Lists, WLAN security, firewalls, IDS/IPS, VPNs, network attacks and hardening techniques.
FROM NETWORKING TO CYBER SECURITY
Now that you have a strong base of understanding in the world of computer networking we can move into the realm of cyber security. Everything that you learned in the Intro to Networking for Cyber Security course will be called upon and stand as your foundation as your transition your learning into Cyber Security!
NexGenT Cyber Security Associate
This online training program provides students with a foundational understanding of the most important topics and concepts, as well as introductory labs, projects, and a cyber range. After completing the Cyber Security course students will use our courses and materials to obtain their NexGenT Cyber certification. During training students will complete over 25 virtualized labs that teach you in demand real world skills that prepare you for the job. Students are also exposed to a cumulative final project that tests them on all the applied learnings they have been taught during the course. After completing the project students then perform a virtual skills qualification check to obtain their cyber certification from NexGenT. During training students also work with our Career Services team for professional career coaching, technical and behavioral practice interviews and professional career maps and guidance check-ins. At the end of this module students will be tested on theory and upon completion receive their NCSA certificate.

Labs25 virtualized labs to help you gain real world skills: Scanning Networks, Social Engineering, Certificate Management, Encryption, Wireshark, Hacking Wireless Networks, Vulnerability Scanning, Network Vulnerabilities, Protocols & Services, Keyloggers, Sniffers, System Hacking, Password Cracking Tools, Evading IDS Firewalls & Honeypots, PKI Concepts. |
IDENTIFY & ANALYZE THREATS
To begin, you will be introduced to a high level overview of the cybersecurity ecosystem. You will understand the threat actors and the different types of attacks you see in this domain. We will also take a look into the various toolkits and how they fit into common cyber security frameworks.
CRYPTOGRAPHY
This module will cover the fundamentals of cryptography along with practical use cases in today’s world. It is an important aspect of security and forms the basis to many protocols that keep us safe. This module will help you understand what happens behind the scenes with these algorithms and how they are useful.
NETWORK SECURITY
Network security is the basis of cyber security operations. In this module we will look at the common security implementations in place and what the common weaknesses are. We will learn about low hanging fruit which are typically overlooked and provide a great way to raise threat awareness.
SECURE PROTOCOLS
This module is meant to help understand basic protocols and the best practices needed to create a security focused organization. The best offense is a defense and we will learn about the different tactics needed to raise the bar.
SYMPTOMS OF COMPROMISE
By recognizing the symptoms of an attack, analysts can help stop them much sooner. Here we will cover what to expect in different scenarios so that you can diagnose the problem in an efficient manner. This analysis is key to understanding what went wrong and how to prevent it from happening again in the future.
TOOLS
By recognizing the symptoms of an attack, analysts can help stop them much sooner. Here we will cover what to expect in different scenarios so that you can diagnose the problem in an efficient manner. This analysis is key to understanding what went wrong and how to prevent it from happening again in the future.
TESTING INFRASTRUCTURE
In this module we will take a look at all the practical applications of attacking your own infrastructure to help defend it. We will teach you how to identify your organizations own weaknesses such that you can help mitigate weaknesses and help define what changes need to be made.
INCIDENT RESPONSE
Incident response is a crucial approach on what to do in the event of a security breach. An organization needs the security team to have a playbook ready in times of crisis and how to react to certain events. We will take a look at planning on what is needed to be done.
NCSA CERTIFICATION: LEVEL UP!To obtain your NexGenT Cyber Security Associate (NCSA) certification you will complete your final presentation and knowledge-based assessment to prove your knowledge and presentation skills and obtain your NCSA certification! |
 |
NexGenT Cyber Security Professional
The NexGenT Cyber Security Professional certification is based on real-world skills which are vetted through the Cyber Range and intermediate knowledge on cyber security topics. Garnering your NCSP means you have learned the skills needed to apply to the real world and have been skills checked in various missions and cyber range scenarios to validate your entry-level cyber security skillset. To obtain the NCSP you must both pass a knowledge-based exam and prove your skills in the cyber range – It’s time to #LevelUp!

Projects
Virtualized projects with various real world missions that test skills learned from labs. These projects build your network engineering and cyber craft for the final cyber range test. Missions will be simulations of attacks such as ransomware, spear phishing, disabling botnets, and defending against web attacks. You will also be given a real world cyber scenario where you come up with a feasible solution and do an elevator pitch presentation to mitigate the problem.
Cyber Range
Learn to defend against malicious threats in real-world lab simulations using our state-of-the-art Cyber Range. A virtualized network where you can gain job ready skills necessary to become a cyber specialist. Here we cover scenarios that mimic ransomware, botnets, password cracking, reverse shells, launching payloads, and a comprehensive review of all types of red / blue team scrimmages. This will help build preparedness by allowing you to test drive incident response playbooks in a real-world situation. This type of immersive training builds situational awareness, which leads to on-the ground experience and offers numerous benefits including real-time feedback and cross-functional training.
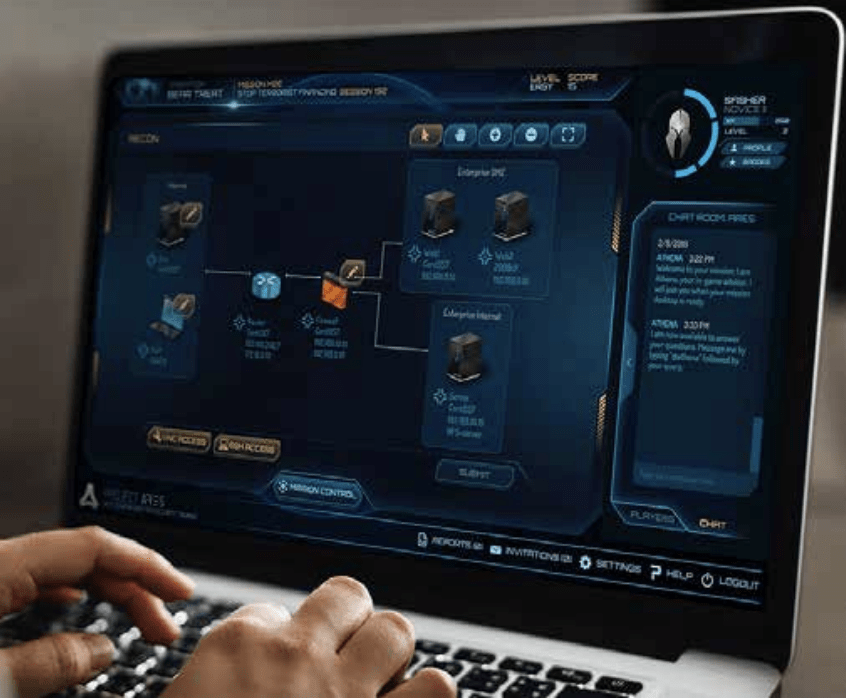
NCSP Skills Qualification CheckDuring this final week all students are scheduled to perform their live SQC (Skills Qualification Check) to verify skills. Upon successful completion the candidate will be awarded the NexGenT Cyber Security Professional (NCSP) Certification. This block of time includes scheduling for all students in the cohort to SQC, get feedback, coaching, and also graduation. Students wil be tested with a cumilitave exam and a final cyber range mission based on skills learned to certify them for job readiness. |
 |
CAREER WORKSHOP 1Students will take their career services assignments (such as the cover letter and resume) and LEVEL THEM UP to interview-landing job applications. We’ll cover how to tailor job applications to the specific jobs they are applying to, identify their own brand and voice, and learn how to articulate their responses to frequently asked interview questions. By the end of this career workshop students will be confident in their resumes, their personal brand, and understand exactly how to approach the application and interview process! |
 |
CompTIA Security+
CompTIA Security+ is the first security certification IT professionals should earn. It establishes the core knowledge required of any cybersecurity role and provides a springboard to intermediate-level cybersecurity jobs. Successful candidates will have the following skills. Get hands-on training* in defensive and offensive cybersecurity, networking, systems, web technologies, and databases, and benefit from our CompTIA Partnership. Through immersive classes and a dynamic curriculum, you’ll develop the fundamental skills to graduate from the program ready to use your knowledge in the workforce.

CAREER WORKSHOP 2Students will go through all the steps to apply for an IT job through our simulated hiring process. They will complete a formal job application and interview for an IT position with the application materials they created in their Career Services’ exercises. Students will identify a job on our company’s website, interview, learn if they were made a job offer or not, and receive detailed feedback. This process will help our candidates emerge from our program with stand out applications, interviews, and winning first impressions to potential employers! |
 |
